The right cybersecurity automation tools enable organizations to identify vulnerabilities swiftly, automate threat detection, and respond to incidents with greater speed and accuracy, which is critical in mitigating the impact of attacks. Moreover, implementing automation in cybersecurity signifies a...
 The Need for Cybersecurity Automation
Traditional IT Security Vs. Automated Cybersecurity
Signs that your organization needs Cybersecurity Automation
Types of Cybersecurity Automation Tools
List of Cybersecurity Automation Tools and its Use Cases
Conclusion
The Need for Cybersecurity Automation
Traditional IT Security Vs. Automated Cybersecurity
Signs that your organization needs Cybersecurity Automation
Types of Cybersecurity Automation Tools
List of Cybersecurity Automation Tools and its Use Cases
Conclusion
The rapid transformation of the digital environment has brought about unparalleled challenges for organizations, emphasizing the crucial importance of staying ahead of cyber threats. With the adoption of hybrid work models, increased reliance on cloud services, and the widespread use of edge devices, the potential attack surface for cybercriminals has expanded significantly. Consequently, cybersecurity professionals are recognizing the essential need to embrace a more preemptive and proactive strategy to secure their fundamental business operations.
The Need for Cybersecurity Automation

Recent research indicates that the average global cost of a data breach in 2023 has reached $4.35 million, showcasing a notable disparity with the United States where the figure stands at a substantial $9.44 million. This stark contrast underscores the significant financial repercussions that organizations face due to cyberattacks.
In response to the escalating threat landscape, leaders across various industries are increasingly adopting artificial intelligence (AI) as a pivotal tool for enhancing security. Notably, a substantial 64% of survey respondents worldwide have already integrated AI into their security capabilities, while an additional 29% are in the process of evaluating its implementation. This underscores the widespread recognition of AI’s effectiveness as a strategic asset in safeguarding against cyber threats.
Traditional IT Security Vs. Automated Cybersecurity

Traditional IT security approaches have historically relied on manual processes and human intervention to identify and mitigate cyber threats. This conventional method often involves setting up firewalls, intrusion detection systems, and antivirus software to protect networks and endpoints. While effective to a certain extent, traditional IT security can be reactive, responding to known threats rather than proactively identifying and preventing emerging risks. Moreover, the sheer volume and sophistication of modern cyber threats make it challenging for human-centric approaches to keep pace, as they may struggle to detect subtle patterns or rapidly evolving attack vectors.
On the other hand, automated cybersecurity represents a paradigm shift in defending against cyber threats. Leveraging advanced technologies such as machine learning and artificial intelligence, automated systems can analyze vast amounts of data in real-time to identify anomalies and potential security breaches. Automated cybersecurity solutions can adapt and learn from new threats, providing a more dynamic defense mechanism. By automating routine tasks such as threat detection, response, and patch management, organizations can enhance their overall security posture while allowing human cybersecurity professionals to focus on more complex and strategic aspects of cybersecurity management. The move towards automated cybersecurity reflects an acknowledgment of the need for speed, efficiency, and adaptability in the face of an ever-evolving threat landscape.
Signs that your organization needs Cybersecurity Automation

Slow Incident Response Times
Swift identification and resolution of security incidents play a crucial role in mitigating the impact of breaches. Nevertheless, a study conducted by NIST revealed a concerning trend: the mean time to detect (MTTD) and mean time to remediate (MTTR) incidents has been on the rise across various organizations. If the time it takes for your incident response is increasing, it serves as a clear indicator that enhancements are needed in your security infrastructure.
Increased Frequency of Data Breaches
As per the 2023 Data Breach Investigations Report by Verizon, there has been a notable surge in global data breaches. The report underscores that these breaches are not only more frequent but also more severe, posing an escalating threat to organizations. This underscores the critical importance of adopting robust cybersecurity measures.
Burdened by an abundance of false positives
Security alerts generating false positives can lead to a misallocation of valuable time and resources, resulting in alert fatigue and diminishing the effectiveness of your security team.
According to the Ponemon Institute’s research, organizations encounter an average of over 17,000 false-positive alerts every week, leading analysts to dedicate up to 25% of their time to investigate and resolve these issues. If your security team is grappling with an excess of false positives, it signals an opportunity for automation to enhance overall efficiency.
Alert fatigue and resource constraints
The ever-evolving nature of threats places significant pressure on cybersecurity professionals to continuously adapt and uphold a strong defense stance. Yet, limitations in resources can impede their capacity to effectively address emerging challenges.
Findings from a survey conducted by the Information Systems Security Association (ISSA) indicate that 62% of organizations have reported a deficiency in skilled cybersecurity personnel. If your security team is grappling with overwhelming challenges, experiencing alert fatigue, or is constrained by insufficient time and resources to proactively tackle threats, the implementation of security automation can alleviate these burdens.
Types of Cybersecurity Automation Tools
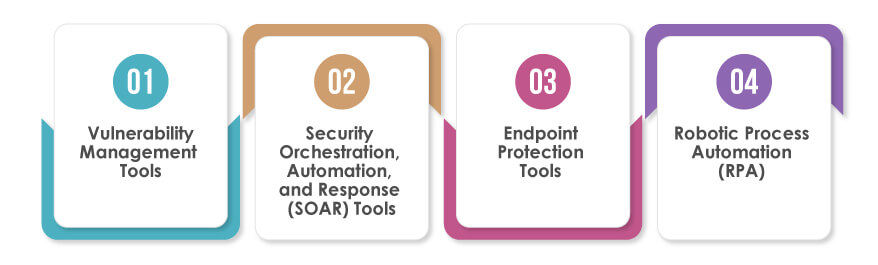
For the successful integration of security automation, organizations can utilize a range of tools and technologies specifically crafted to streamline security operations, boost capabilities in threat detection and response, and automate repetitive tasks. The following are examples of commonly used cybersecurity automation tools:
Vulnerability Management Tools
Tools for vulnerability management automate the identification, categorization, and prioritization of vulnerabilities within an organization’s IT infrastructure. They conduct scans on networks, systems, and applications to detect vulnerabilities, evaluate their severity, and suggest remediation actions. The automation of vulnerability management enables organizations to take proactive measures in addressing security weaknesses, thereby minimizing the timeframe in which potential attacks could exploit vulnerabilities.
Benefits:
Efficiently detect and prioritize vulnerabilities in a timely manner.
Expedite the remediation process with automated recommendations.
Enhance overall security posture by taking proactive measures to address vulnerabilities.
Security Orchestration, Automation, and Response (SOAR) Tools
SOAR (Security Orchestration, Automation, and Response) tools enhance the efficiency of security operations by automating and orchestrating tasks associated with threat management, incident response, and overall security operations. These tools seamlessly integrate with diverse security technologies and systems, enabling organizations to establish standardized playbooks and automated workflows for incident response and mitigation.
Benefits:
• Speed up incident response through the automation of repetitive tasks.
• Foster improved collaboration and coordination among security teams.
• Enhance efficiency and consistency in incident management and resolution.
Endpoint Protection Tools
Endpoint protection tools concentrate on safeguarding individual endpoints, such as PCs, laptops, mobile devices, and IoT devices, against a range of threats, including malware, ransomware, and unauthorized access. Incorporating features like antivirus, anti-malware, firewall, and device management capabilities, these tools offer comprehensive protection for endpoints.
Benefits:
• Identify and address threats at the endpoint level.
• Centrally oversee and administer endpoint security.
• Safeguard sensitive data and thwart unauthorized access.
Robotic Process Automation (RPA)
RPA (Robotic Process Automation) technology employs software robots to automate routine, rule-based tasks that lack the need for intricate analysis. While not inherently tailored for cybersecurity, RPA can be harnessed for certain security functions, including vulnerability scanning, the operation of monitoring tools, and basic threat mitigation. RPA can carry out predetermined tasks triggered by specific events or scheduled occurrences.
Benefits:
• Automate everyday security tasks and procedures.
• Enhance efficiency by minimizing manual effort and human errors.
• Boost scalability and accelerate the pace of security operations.
List of Cybersecurity Automation Tools and its Use Cases

| Problem Area | Use Case | Cybersecurity Automation Tool |
| Vulnerability Management | Automating the process of identifying, classifying, prioritizing, and remediating vulnerabilities within IT resources. | Vulnerability management tools |
| Threat Detection | Improving the identification and detection of potential threats and anomalies throughout the organization’s IT infrastructure. | Security Information and Event Management (SIEM) |
| Incident Response | Efficiently optimizing incident response procedures and decreasing the mean time to detect and address security incidents. | Security Orchestration, Automation, and Response (SOAR) |
| Compliance Management | Automating tasks related to compliance, including adherence to data privacy regulations, industry standards, and internal policies. | Security Orchestration, Automation, and Response (SOAR) or Vulnerability Management Tools |
| Security Operations | Automating routine tasks in security operations, such as analyzing logs, managing incident tickets, and executing security workflows. | Security Orchestration, Automation, and Response (SOAR) |
| Data Loss Prevention | Automating the identification, monitoring, and prevention of unauthorized access, data leakage, or theft across the network and endpoints of the organization. | Endpoint Protection Tools or Security Orchestration, Automation, and Response (SOAR) |
Conclusion
Considering hackers’ growing use of AI and other generative technologies for malicious purposes, it is essential for security practices to adapt by integrating the latest automation tools and techniques to remain competitive and efficient. The right automation tools in cybersecurity enable organizations to identify vulnerabilities swiftly, automate threat detection, and respond to incidents with greater speed and accuracy, which is critical in mitigating the impact of attacks. Moreover, implementing automation in cybersecurity signifies a strategic shift towards more proactive and predictive security postures. This shift is crucial for organizations to manage the ever-growing volume of data and the complexity of modern network environments.
Tx-Secure – A Security Testing Accelerator to Enhance Cybersecurity
To safeguard your organization against evolving cyber threats, TestingXperts Test Center of Excellence (TCoE), has developed Tx-Secure, a security testing accelerator designed to enhance and streamline the security testing process. Here’s what makes Tx-Secure an essential tool for modern businesses for streamlining cybersecurity automation process:
• Tx-Secure integrates specific processes and guidelines, complemented by various tools and checklists, to facilitate seamless security testing.
• The accelerator is engineered to expedite the security testing process, ensuring quicker and more significant outcomes.
• This framework is adept at testing applications across various platforms, including Blockchain, IoT, and Network Infrastructure security.
• Tx-Secure also offers the flexibility to establish secure testing labs tailored to specific customer needs.
• All security testing services under Tx-Secure align with global standards like GDPR, HIPAA, PCI-DSS, OSSTMM, OWASP, etc., ensuring top-notch security and compliance.
To know more, Contact our Cybersecurity experts now.
The post Importance of Choosing the Right Cybersecurity Automation Tool in 2024 first appeared on TestingXperts.